In this post I will tell you about an Android app that is extremely useful to run commands remotely on a Linux computer: Hot Button SSH Command Widget. This application allows you to launch conveniently any command you want on a remote computer through SSH only with the push of a button on the screen of your mobile phone or tablet. This not only will facilitate automation of repetitive tasks, but also is very interesting from the perspective of security for the same reasons I exposed in my Automatically lock/unlock your screen by Bluetooth device proximity post. It will allow you for example to lock and unlock the screen without having to type your password again and again in sight of other people.
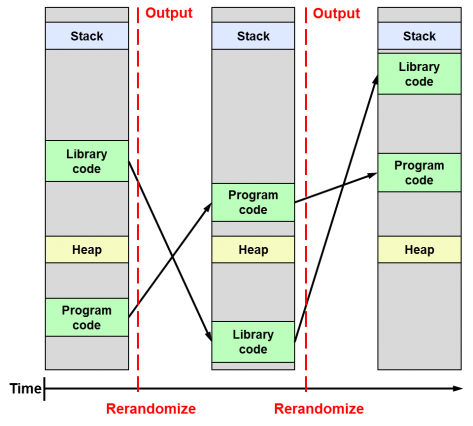
Differences between ASLR, KASLR and KARL
Following the release of the Linux Kernel 4.12, which for the first time brings the KASLR feature enabled by default, and almost simultaneously the announcement of a feature called KARL in OpenBSD, I found it interesting to clarify the differences between these security techniques, since I think that the combination of both will be very important in the future of system security as they will prevent exploiting vulnerabilities related to memory corruption (buffer-overflow).
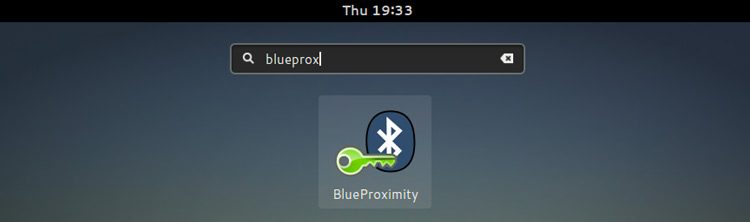
Automatically lock/unlock your screen by Bluetooth device proximity
One of the most basic and common security measures that you can adopt in your working environment is to protect your computer by automatically locking the screen after a certain period of inactivity, so that it is necessary to enter a password to unlock. But there is a more effective way, and that is to configure your Linux machine so that the distance or proximity of a Bluetooth device you own, for example your cell phone or a smartwatch, automatically causes locking or unlocking the screen without having to enter any password on keyboard.
The importance of properly partitioning a disk in Linux

It is a common practice that the various distributions of Linux, and even the images used to launch Linux virtual server instances as in the case of AWS AMI’s, implement by default an extremely simple partitioning scheme consisting in a single partition that covers the entire disk. It is in this only partition where the root filesystem (/) is mounted and in which all the directories that configure the file hierarchy of a Linux operating system are placed.
But one of the features of Linux is precisely that it allows you to be highly flexible in placing each of these directories on different partitions or on different disks if necessary.
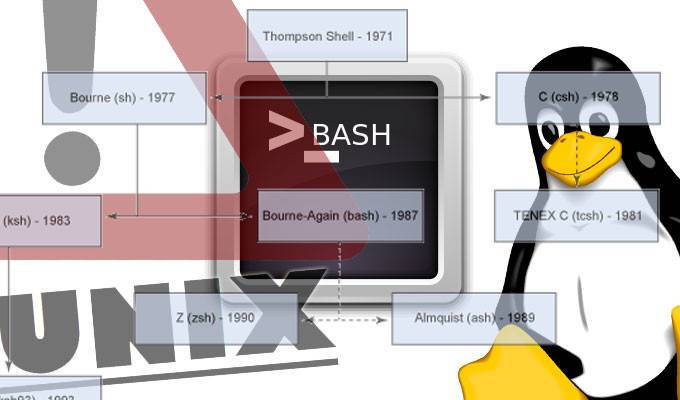
Still unresolved Shellshock major vulnerability affecting Bash on Linux, Unix and MAC OS X
Less than two days after it was detected a vulnerability (CVE-2014-6271) that affects the Bash shell on Linux, Unix and Mac OS X, a patch was released that solves this issue only partially, which forced to report a new vulnerability (CVE-2014-7169) still pending. This issue has quickly gained a simple name by which it will be remembered for a long time: Shellshock or Shell Shock.
Perfom Windows backups using rsync and DeltaCopy Server
Rsync and Windows?
Many corporate and heterogeneous networks use the rsync protocol to perform server backups or to keep files synchronized automatically from one or more directories on different machines. Linux natively incorporates the rsync utility and other associated tools, but what do you do when you need to backup Windows folders automatically from a NAS or a remote machine? One option could be to use Samba to read the contents of those folders from Linux, but it would be a fairly complex solution, because it would force us to configure Samba on the server side, set the various permissions and configuration options in Windows and place both machines on the same local network or configure complex rules on our firewall to allow SMB/CIFS traffic. And yet, the file transfer through the network would not be safe, because it would be made text clear with no encryption.
How to create a Windows SSH server
Neither version of Windows, either Windows XP, Windows 7, or 8 or more modern versions such as Windows Server 2008 or Windows 2012, provides an SSH server to use a standard way to access from other machines with different operating system and be able to run console commands, copy files, forward ports or automate logins by using public/private keys. The Microsoft alternative to this is WinRM / Powershell, but many are the chances that we will need to find a standard and compatible way to access to other systems, and what better way to do this than using the widespread and well-known SSH protocol to get into our Windows machines securely.
1-click automatically open a Keepassx database
Those who use the tool KeePassX (KeePass clone for Linux and Mac OS X) to safely save passwords and login details at one single place will have seen many times on the need for rapid access to their repository of passwords with a single click. However, by default when accessing KeePassX none repository is open, or one is open that does not correspond to the one we want to check, so often it’s necessary to browse the file system to locate and select the corresponding file. If in addition to a master password we use a key file to improve security, we have to repeat the same process over and over again to locate and select the key file.